 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
The latest Facebook privacy SNAFU (Situation Normal, All Facebooked Up) is a bug that changed settings on some accounts, automatically suggesting that their updates be posted publicly, even though users had previously set their updates as “private”.
On Thursday, Facebook asked 14 million users to review posts made between 18 May and 22 May: that’s when the bug was changing account settings. Not all of the 14 million users affected by the bug necessarily had their information publicly, mistakenly shared, but best to check.
Facebook Chief Privacy Officer Erin Egan said in a post that as of Thursday, the company had started letting those 14 million people know about the situation. She stressed that the bug didn’t affect anything people had posted before that time, and even then, they could still have chosen their audience like they always have.
Normally, the audience selector is supposed to be sticky: every time you share something, you get to choose who sees it, and the suggestion is supposed to be based on who you shared stuff with the last time you posted. Friends only? Fine, that’s what should be automatically suggested for the next post, and the one after that, until you change it… or a weird little glitch like this pops up. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Spätestens seit dem Cambridge-Analytica-Skandal stehen viele Menschen Facebook skeptisch gegenüber. Wie Forscher nun herausgefunden haben können beim "Login mit Facebook" Skripte von Drittfirmen die Facebook-Identität des Besuchers nachverfolgen.
Wenn ein Internet-Nutzer auf einer Webseite die Funktion "Login mit Facebook" verwendet, gibt er der Webseite, auf der er sich befindet, unter Umständen Zugriff auf sein öffentliches Facebook-Konto. Forscher der Princeton-Universität in den USA warnen nun davor, dass auf dieser Webseite eingebettete Skripte von Dritten ebenfalls Zugriff auf diese Daten haben. Laut den Forschern sammeln Tracker so die Informationen der Webseitenbesucher – in den meisten Fällen wohl ohne dass die betroffene Webseite davon Kenntnis hat. Derartige Scripte fanden sie auf 434 der eine Million meistbesuchten Seiten im Netz.
Die meisten der Dritt-Skripte fragen den Facebook-Namen und die E-Mail-Adresse des Besuchers ab, der sich über Facebook auf der Seite anmeldet. Zwar ist die ID, welche die Skripte abgreifen, erst einmal auf die Anmelde-Routine der besuchten Webseite beschränkt; wie die Forscher zeigen, lassen sich darüber allerdings die öffentlichen Facebook-Informationen des Besuchers extrahieren. Dazu gehört dessen Facebook-Name und sein Profilbild. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
A little-known data firm was able to build 48 million personal profiles, combining data from sites and social networks like Facebook, LinkedIn, Twitter, and Zillow, among others -- without the users' knowledge or consent.
Localblox, a Bellevue, Wash.-based firm, says it "automatically crawls, discovers, extracts, indexes, maps and augments data in a variety of formats from the web and from exchange networks." Since its founding in 2010, the company has focused its collection on publicly accessible data sources, like social networks Facebook, Twitter, and LinkedIn, and real estate site Zillow to name a few, to produce profiles.
But earlier this year, the company left a massive store of profile data on a public but unlisted Amazon S3 storage bucket without a password, allowing anyone to download its contents.
The bucket, labeled "lbdumps," contained a file that unpacked to a single file over 1.2 terabytes in size. The file listed 48 million individual records, scraped from public profiles, consolidated, then stitched together. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Cybercriminals are using Facebook Messenger to spread adware, duping victims by redirecting them to fake versions of popular websites that are tailored to their browser.
The attacks were uncovered by a security researcher who received a suspicious Facebook message from a contact and analysed its contents.
"This malware was spreading via Facebook Messenger, serving multi platform malware/adware, using tons of domains to prevent tracking, and earning clicks. The code is advanced and obfuscated," said David Jacoby, senior security researcher in the global research and analysis team at Kaspersky Lab.
Researchers have suggested that malicious links are being sent from Messenger accounts that have been compromised as a result of stolen credentials, hijacked browsers, or clickjacking. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook
Twitter’s been combatting harassment for years. The latest effort: quelling its horde of anonymous, hostile egg accounts. But for many users, Twitter’s abuse problem has long since undermined its value as a platform for creative communication. That’s what makes Mastodon—a free, open-source, and increasingly popular six-month-old Twitter alternative—so intriguing.
Mastodon has created a diverse yet welcoming online environment by doing exactly what Twitter won’t: letting its community make the rules. The platform consists of various user-created networks, called instances, each of which determines its own laws. One instance could ban sexist jokes and Nazi logos, while another might practice radically free speech. (In this way, Mastodon is not unlike a network of discretely moderated message boards crossed with a Tweetdeck-like interface.) Users choose for themselves which instance they want to join and select from a host of privacy and anti-harassment settings. Oh, and the character limit is 500, not 140. In essence, Mastodon is an experiment in whether individually moderated communities can make a social network like Twitter more civil. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/social-media-and-its-influence/?&tag=Mastodon

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Über das Unternehmen Geofeedia konnten US-Behörden Standortdaten von Facebook- und Twitter-Nutzern sammeln.
Facebook, Instagram und Twitter kennen viele Details ihrer Nutzer. Dies hat offenbar auch die US-Regierung erkannt und die Datenströme der Dienste über die Analytics-Plattform Geofeedia angezapft . Laut der Bürgerrechtsorganisation American Civil Liberties Union (ACLU) nutzte unter anderem die Polizei diese Informationen, um die Rassenproteste in Oakland und Baltimore zu überwachen.
Die Sammlung der Daten wurde von dem in Chicago ansässigen Unternehmen Geofeedia übernommen, das die Informationen dann an rund 500 Strafverfolgungs- und Sicherheitsbehörden weitergereicht haben soll. Neben persönlichen Informationen wurden auch Standortdaten von Nutzern gesammelt.
Facebook und Twitter beteuern, dass es sich bei dem abgegriffenen Daten um öffentlich zugängliche Informationen handeln würde. Als Reaktion auf die Vorwürfe schränkten beide Unternehmen den Zugriff von Geofeedia auf die Datenströme der sozialen Netzwerke ein oder sperrten den Anbieter sogar. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ http://www.scoop.it/t/securite-pc-et-internet/?tag=Privacy

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Sicherheitsforscher wollen entdeckt haben, wie man jedes Facebook-Konto hacken kann, für das eine Handynummer hinterlegt ist.

|
Scooped by
Gust MEES
|
Ein Sicherheitsforscher entdeckte eine Sicherheitslücke, über die er einen internen Facebook-Server übernehmen konnte. Bei genauerem Hinsehen fand er dann die Hintertüren seiner Vorgänger.
|

|
Scooped by
Gust MEES
|
Twitter has admitted that user passwords were briefly stored in plaintext and may have been exposed to the company's internal tools.
In a blog post, the microblogging site urged users to change their passwords.
"When you set a password for your Twitter account, we use technology that masks it so no one at the company can see it. We recently identified a bug that stored passwords unmasked in an internal log," said Twitter in a statement.
Twitter didn't say how many accounts were affected, but Reuters reports -- citing a source -- that the number of affected users was "substantial" and that passwords were exposed for "several months."
It's unclear exactly why user passwords were stored in plaintext before they were hashed. Twitter said that it stores user passwords with bcrypt, a stronger password hashing algorithm, but a bug meant that passwords were "written to an internal log before completing the hashing process."
The company said it fixed the bug and that an investigation "shows no indication of breach or misuse" by anyone.
A spokesperson for Twitter reiterated that the bug "is related to our internal systems only," but it did not comment further.
"Since this is not a breach and our investigation has shown no signs of misuse, we are not forcing a password reset but are presenting the information for people to make an informed decision about their account," said the spokesperson. "We believe this is the right thing to do."
The company had 330 million users at its fourth-quarter earnings in February.
Read also: Twitter hopes trolls can be stopped by eradicating ignorance
Twitter is the second company to admit a password-related bug this week.
GitHub on Tuesday said it also exposed some users' plaintext passwords after they were written to an internal logging system.
It's not known if the two incidents are related, and a Twitter spokesperson would not comment in a follow-up email. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet?page=2&tag=Passwords https://www.scoop.it/t/securite-pc-et-internet/?&tag=Password+Managers https://www.scoop.it/t/securite-pc-et-internet/?&tag=Twitter

|
Scooped by
Gust MEES
|
LinkedIn bug allowed data to be stolen from user profiles
Private profile data — like phone numbers and email addresses — could have been easily collected.
A bug in how LinkedIn autofills data on other websites could have allowed an attacker to silently steal user profile data.
The flaw was found in LinkedIn's widely used AutoFill plugin, which allows approved third-party websites to let LinkedIn members automatically fill in basic information from their profile -- such as their name, email address, location, and where they work -- as a quick way to sign up to the site or to receive email newsletters.
LinkedIn only allows whitelisted domains to have this functionality, and LinkedIn has to approve each new domain. Right now, there are dozens of sites in the top 10,000 websites ranked by Alexa that have been whitelisted by LinkedIn, including Twitter, Microsoft, LinkedIn, and more.
That means any of those websites can retrieve this profile data from users without their approval.
But if any of the sites contains a cross-site scripting (XSS) flaw -- which lets an attacker run malicious code on a website -- an attacker can piggy-back off that whitelisted domain to obtain data from LinkedIn.
And it turns out that at least one of them did. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=LinkedIn

|
Scooped by
Gust MEES
|
Facebook appears to be getting tougher on people who break its rules.
Hot on the heels of banning the Britain First group from its network, Facebook has announced it has suspended political data analytics firm Cambridge Analytica, and its parent company Strategic Communication Laboratories (SCL).
But the reason for the organisations being blocked from Facebook are very different. Britain First is accused of spreading vile hateful messages about Muslims, but Cambridge Analytica is accused of acquiring the data of more than 50 million Facebook users via an illegitimate route.
Cambridge Analytica is the shady data analytics firm that specialises in “psychographic” profiling. In short, they scoop up data online and use it to create personality profiles for voters.
That knowledge could be extremely useful, as individuals can then be targeted with content targeted to appeal to them, and perhaps influence their behaviour. Maybe even change their likelihood to vote in a particular direction.
Cambridge Analytica is widely credited for helping Donald Trump’s successful campaign on social media to be elected President of the United States. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Big+Data https://www.scoop.it/t/securite-pc-et-internet/?&tag=Ethics

|
Scooped by
Gust MEES
|
Facebook-Nutzer, aufgepasst! Aktuell verbreitet sich ein schadhafter Link über den Facebook Messenger. Das Problem: Er kommt von den eigenen Freunden. Selbst die Polizei hat eine entsprechende Warnung herausgegeben. Die Details!
Schlechte Nachrichten für Facebook-Fans: Das soziale Netzwerk ist aktuell von einer Betrugsmasche betroffen, die sich über den Facebook Messenger ausbreitet und Nutzern jede Menge Ärger beschert. Das Fiese an der Sache ist vor allem, dass der Link dazu direkt von Ihren Freunden kommt – zusammen mit einem zwinkernden Smiley und dem Text „Du video? (Link) Kevin”. Wegen verstärkter Anfragen zum Thema hat auch die Polizei Niedersachsen eine Warnung vor dem Facebook-Betrug herausgegeben.
Facebook Messenger: Finger weg von dubiosen Links!
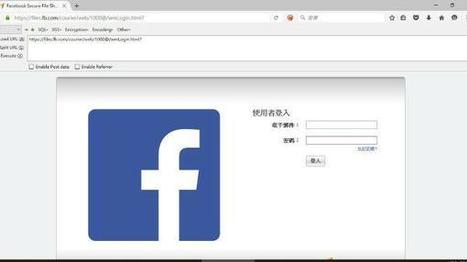
Wenn Sie den Link öffnen, landen Sie auf einer Seite, die genau wie die Log-in-Page von Facebook aussieht. Tatsächlich läuft die jedoch unter einer völlig anderen Adresse. Geben Sie dort Ihre Daten ein, landen Sie direkt bei den Betrügern. Die haben von diesem Zeitpunkt an vollen Zugriff auf Ihr Facebook-Konto und können allerlei Schabernack damit treiben. Dazu gehört auch das Weiterversenden der schadhaften Nachricht. Auch die neue Seite „Sicherheitszentrum” versucht es mit diesem Link. Die Page soll den Anschein erwecken von Facebook zu stammen und droht mit der Löschung von zuvor markierten Profilen. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Une note de sécurité du Kaspersky Lab, sur sa plateforme SecureList, met en garde contre un malware multiplateforme qui se répand via Facebook Messenger.
Pratiquement, le malware vous envoie un message sur Messenger, sous l'identité d'un ami... Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Dieser neue Virus nutzt eure Gewohnheiten aus und verbreitet sich ganz unbemerkt. Nicht nur auf dem Computer zuhause, sondern auch bei Freunden, Kollegen oder Verwandten. Dabei fängt alles ganz harmlos an. Virus kommt per Messenger Der Virus kommt über den Facebook-Messenger. In Form einer eigentlich ganz normalen Nachricht. Es sieht so aus, als würde ein guter Freund, der euch sogar mit Namen anspricht, einen Link schicken. In der Regel zu einem Video. Dazu ein Emoji, das uns neugierig machen soll, auf das, was sich hinter dem Videolink verbirgt. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook
A new social media network named Mastodon popped up a few months ago and is designed to deliver a decentralised, open-source experience, but its this unique structure that may make its members vulnerable to cyber-attacks.
Malwarebyte's researcher Zammis Clark blogged that the decentralised nature of the site's construction, which he said helps eliminate ads, a primary selling point for users, also leaves the social network open to hackers. The site is very different from Facebook, Twitter and other networks.
Instead of being hosted by a corporate entity on its server system Mastodon members can set up their own server if they wish, called in “instance” by the Mastodon community, and then have people join Mastodon through that server. But here is where the problem arises.
Each person's “instance” receives a special domain name, for example mastodon.instance1, and anyone registering on that instance would receive a username like johnsmith.mastodon.instance1.
Where things go awry, Clark said, is the usernames can be replicated across all the "instances", so on mastodon.instance2 there could be a johnsmith.mastodon.instance2. This creates a situation where there are no verified accounts.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Vorsicht! Auf diese Links sollten Sie nie klicken
Cyberkriminelle versuchen es leider immer wieder, Schadsoftware zu verbreiten. Dieses Mal haben sie es auf die User der Facebook-Messenger-App abgesehen. Deswegen: Klicken Sie nie auf Links denen Sie nicht hundertprozentig vertrauen können. Weitere Infos und Tipps zu der Masche bekommen Sie im Video.
Sie haben sich bereits einen Virus eingefangen? Wir zeigen Ihnen hier was Sie tun können, wenn Sie einen Virus auf Ihrem Android-Gerät haben.

|
Scooped by
Gust MEES
|
Forscher von Eset weisen auf ein Android-Botnetz hin, das nicht von einem Kommandoserver, sondern über Twitter gesteuert wird. Diese von PC-Schädlingen seit mindestens 2009 bekannte Verfahren wird damit nach ihrer Einschätzung erstmals für einen Android-Trojaner verwendet.
Aufgrund des für die Koordination verwendeten Kommunikationskanals haben die Forscher den Trojaner Twitoor getauft. Ist er einmal installiert, fragt er regelmäßig ein spezielles Twitter-Konto ab, um eventuelle Befehle zu empfangen. Die Hintermänner können den Trojaner so beispielsweise anweisen, weitere bösartige Anwendungen zu installieren (in der Praxis bisher vor allem solche, die Bankdaten stehlen) oder auch, den Twitter-Kanal zu wechseln.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnets http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Botnet

|
Scooped by
Gust MEES
|
A database with 154 million US voter registration records has been leaking information on a dizzying array of intimate details, including gun ownership, Facebook profiles, address, age, position on gay marriage, ethnicity, email addresses and whether a voter is “pro-life.”
MacKeeper security researcher Chris Vickery found the instance of a CouchDB database wide open, configured as it was for public access with no username, password, or other authentication required.
As Vickery said in a post, he tracked down and notified the company that was the source of the database. It was shut down within 3 hours.
On Tuesday, Vickery reached out to the company – a data brokerage firm named L2 – to report his theory: that one of its clients had purchased data from L2 and was hosting it in an insecure manner.
L2 said that yes, that was the case. He and L2 CEO Bruce Willsie tracked down the client, and the database was taken offline within 3 hours. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
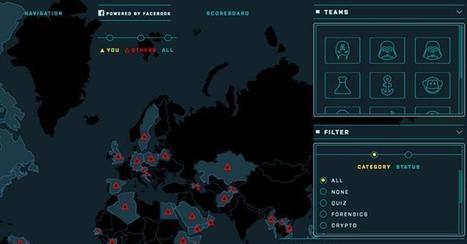
Facebook wants to teach the next generation security skills and hopes the release of the Capture the Flag (CTF) platform to the open-source community will be a valuable contribution.
Gulshan Singh, a software engineer on Facebook's threat infrastructure team said in an announcement on Wednesday the social media giant hopes to make "security education easier and more accessible," especially for students.
As a result, the company has decided to release the CTF platform as a "safe and legal" way to teach kids how to learn and refine skills related to reverse-engineering, forensics, web application security, cryptography, and binary exploitation without getting into trouble with the law.
It is rare for schools to build and run their own CTF environments, and there are few currently available on the market. Beyond web domains configured for network professionals to test out their skills, such as Hack this site.org, security education resources geared towards students can be a challenge.
|



 Your new post is loading...
Your new post is loading...









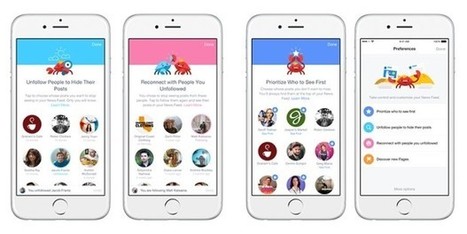















The latest Facebook privacy SNAFU (Situation Normal, All Facebooked Up) is a bug that changed settings on some accounts, automatically suggesting that their updates be posted publicly, even though users had previously set their updates as “private”.
On Thursday, Facebook asked 14 million users to review posts made between 18 May and 22 May: that’s when the bug was changing account settings. Not all of the 14 million users affected by the bug necessarily had their information publicly, mistakenly shared, but best to check.
Facebook Chief Privacy Officer Erin Egan said in a post that as of Thursday, the company had started letting those 14 million people know about the situation. She stressed that the bug didn’t affect anything people had posted before that time, and even then, they could still have chosen their audience like they always have.
Normally, the audience selector is supposed to be sticky: every time you share something, you get to choose who sees it, and the suggestion is supposed to be based on who you shared stuff with the last time you posted. Friends only? Fine, that’s what should be automatically suggested for the next post, and the one after that, until you change it… or a weird little glitch like this pops up.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook