 Your new post is loading...
 Your new post is loading...
The Simda botnet, believed to have infected more than 770,000 computers worldwide, has been targeted in a global operation.
In a series of simultaneous actions around the world, on Thursday 9 April, 10 command and control servers were seized in the Netherlands, with additional servers taken down in the US, Russia, Luxembourg and Poland.
The operation involved officers from the Dutch National High Tech Crime Unit (NHTCU) in the Netherlands, the Federal Bureau of Investigation (FBI) in the US, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department “K” supported by the INTERPOL National Central Bureau in Moscow.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
'Watch Dogs' players targeted for access to their juicy GPUs
"If you happen to download cracked games via Torrent or other P2P sharing services, chances are that you may become a victim of [a] lucrative trojan bundled with a genuine GPU miner," BitDefender chief strategist Catalin Cosoi said of an early Bitcoin miner that targeted gamers.

|
Scooped by
Gust MEES
|
Les chercheurs de l'entreprise de sécurité IntelCrawler ont mis à jour un botnet réunissant environ 1 500 points de vente et autres systèmes de vente au détail compromis dans 36 pays dans le monde.
IntelCrawler a évalué la taille du botnet Nemanja à 1 478 systèmes PoS infectés. L'entreprise de sécurité a localisé ces systèmes dans différents pays, dont les États-Unis, le Royaume-Uni, le Canada, l'Australie, la Chine, la Russie, le Brésil et le Mexique. Mais le botnet Nemanja a également été détecté dans d'autres pays comme l'Argentine, l'Autriche, le Bangladesh, la Belgique, le Chili, la République tchèque, le Danemark, l'Estonie, la France, l'Allemagne, Hong Kong, l'Inde, l'Indonésie, Israël, l'Italie, le Japon, les Pays-Bas, la Nouvelle-Zélande, la Pologne, le Portugal, l'Afrique du Sud, l'Espagne, la Suisse, Taiwan, la Turquie, l'Uruguay, le Venezuela et la Zambie.

|
Scooped by
Gust MEES
|
Akamai announced a new global DDoS attack report, which shows that in Q1, DDoS attackers relied less upon traditional botnet infection in fa...
Legitimate sites forced to aid criminals' illicit botnet operations
Hackers have hijacked more than 162,000 legitimate WordPress sites, connecting them to a criminal botnet and forcing them to mount distributed denial-of-service (DDoS) attacks, according to security firm Sucuri.
Sucuri CTO Daniel Cid said the company uncovered the botnet when analysing an attack targeting one of its customers. Cid said Sucuri managed to trace the source of the attack to legitimate WordPress sites. "The most interesting part is that all the requests were coming from valid and legitimate WordPress sites. Yes, other WordPress sites were sending random requests at a very large scale and bringing the site down," read the blog.
Via Gust MEES
A new report from Dell SecureWorks Counter Threat Unit CTU research team breaks down the biggest banking botnets from last year, and reveals that 900 financial institutions from around the globe have been targeted.
Via Frederic GOUTH, Gust MEES
Multi-platform threat exploits old Java flaw, gains persistence. Researchers have uncovered a piece of botnet malware that is capable of infecting computers running Windows, Mac OS X, and Linux that have Oracle's Java software framework installed. The cross-platform HEUR:Backdoor.Java.Agent.a, as reported in a blog post published Tuesday by Kaspersky Lab, takes hold of computers by exploiting CVE-2013-2465, a critical Java vulnerability that Oracle patched in June. The security bug is present on Java 7 u21 and earlier. Once the bot has infected a computer, it copies itself to the autostart directory of its respective platform to ensure it runs whenever the machine is turned on. Compromised computers then report to an Internet relay chat channel that acts as a command and control server.

|
Scooped by
Gust MEES
|
Since Microsoft took positive action against the ZeroAccess botnet at the beginning of December, SophosLabs has been paying close attention to see if the owners would attempt to revitalise the botn...

|
Scooped by
Gust MEES
|
Au travers d’un partenariat de sécurité public-privé, Europol et le FBI, associés à des acteurs technologiques dont Microsoft, ont mené une action contre le botnet ZeroAccess. Mais si son fonctionnement est perturbé, il n’est cependant pas démantelé.

|
Scooped by
Gust MEES
|
Microsoft, in conjunction with Europol and the FBI, have successfully taken down the click fraud servers used by ZeroAccess, disrupting one of the world's largest and most resilient botnets. In the meantime though we should give praise to Microsoft and its crime busting partners for the serious blow they have landed on a difficult opponent. Unless Microsoft or Europol can identify the 'John Does 1-8' mentioned in the court documents then we can expect ZeroAccess to resurface in the near future.

|
Scooped by
Gust MEES
|
Google Cloud Messaging serving as conduit for sending data from C&C servers Criminals rent such networks to others for malware distribution. Among the malware distributed is the most sophisticated Android Trojan, known as Obad, Kaspersky said. The malware opens a backdoor in an infected device in order to download additional malicious code for stealing money from victims' bank accounts. While not common in the U.S., people in other countries often use their smartphone for money transfers.
|

|
Scooped by
Gust MEES
|
3 million strong RAMNIT botnet taken down
Posted on 25.02.2015
The National Crime Agency’s National Cyber Crime Unit (NCCU) worked with law enforcement colleagues in the Netherlands, Italy and Germany, co-ordinated through Europol’s European Cybercrime Centre (EC3), to shut down command and control servers used by the RAMNIT botnet.
RAMNIT spread malware via seemingly trustworthy links sent out on phishing emails or social networking websites. If users running Windows clicked on the links, the malware would be installed, infecting the computer. Infected computers would then be under the control of criminals, enabling them to access personal or banking information, steal passwords and disable antivirus protection.
Investigators believe that RAMNIT may have infected over three million computers worldwide, with around 33,000 of those being in the UK. It has so far largely been used to attempt to take money from bank accounts. Analysis is now taking place on the servers and an investigation is ongoing.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Bulgarian and French judicial and law enforcement authorities, working in close cooperation with the European Cybercrime Centre (EC3) at Eur...
The primary modus operandi of the criminals and their associates was to harvest financial data from ATMs in different areas of France (e.g. Nancy, Metz, and Lyon) as well as other EU countries, which they then used to create fake payment cards. The fake cards could then be used to withdraw large amounts of cash from ATMs outside the European Union (e.g. in the Philippines, Malaysia and Indonesia).
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=POS

|
Scooped by
Gust MEES
|
Security researchers at Incapsula discovered a DDoS attack on a video site that used a persistent XSS vulnerability and malicious Javascript.

|
Scooped by
Gust MEES
|
Cyber criminals can infiltrate your mobile devices with the just discovered first "TOR Trojan for Android".

|
Scooped by
Gust MEES
|
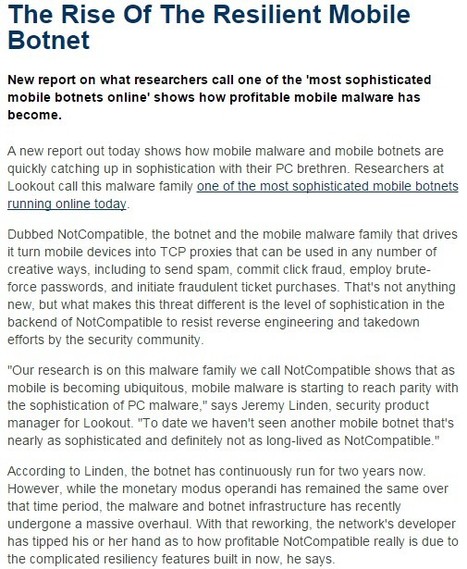
A new trojan for Android has been discovered that resides in the memory of infected devices and launches itself early on in the OS loading stage. Even if some elements of the threat ...

|
Scooped by
Gust MEES
|
Ein US-Sicherheitsunternehmen hat ein Botnetz enttarnt. Das Besondere daran ist, dass etwa ein Viertel der infizierten Geräte keine Computer sind, sondern andere Internet-fähige Geräte - darunter

|
Scooped by
Gust MEES
|
Last week, we learned that police in Germany arrested two individuals who used a modified version of an existing malware to create a botnet which they... Skynet is capable of performing various tasks, including launching DDOS attacks, mining Bitcoin and stealing banking information.

|
Scooped by
Gust MEES
|
News and perspectives covering the top stories, events and activities from Microsoft. The content for this blog includes the official information and stories from all of Microsoft's primary businesses.

|
Scooped by
Gust MEES
|
Trojan backdoors have traditionally attacked desktop and now mobile computers. In recent months, however, attackers have started to target servers.
|



 Your new post is loading...
Your new post is loading...
























The Simda botnet, believed to have infected more than 770,000 computers worldwide, has been targeted in a global operation.
In a series of simultaneous actions around the world, on Thursday 9 April, 10 command and control servers were seized in the Netherlands, with additional servers taken down in the US, Russia, Luxembourg and Poland.
The operation involved officers from the Dutch National High Tech Crime Unit (NHTCU) in the Netherlands, the Federal Bureau of Investigation (FBI) in the US, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department “K” supported by the INTERPOL National Central Bureau in Moscow.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet