 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
The Hive ransomware gang now also encrypts Linux and FreeBSD using new malware variants specifically developed to target these platforms.
However, as Slovak internet security firm ESET discovered, Hive's new encryptors are still in development and still lack functionality.
The Linux variant also proved to be quite buggy during ESET's analysis, with the encryption completely failing when the malware was executed with an explicit path.

|
Scooped by
Gust MEES
|
Clubhouse CEO Paul Davison said Sunday that a report claiming personal user data had been leaked was “false.” Cyber News reported a SQL database with users’ IDs, names, usernames, Twitter and Instagram handles and follower counts were posted to an online hacker forum. According to Cyber News, it did not appear that sensitive user information such as credit card numbers were among the leaked info.
Clubhouse did not immediately reply to a request for more information from The Verge on Sunday. But Davison said in response to a question during a town hall that the platform had not suffered a data breach. “No, This is misleading and false, it is a clickbait article, we were not hacked. The data referred to was all public profile information from our app. So the answer to that is a definitive ‘no.’” Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
The personal data of 1.3 million Clubhouse users has leaked online on a popular hacker forum, according to a Saturday report from Cyber News.
The leaked data of Clubhouse users includes names, social media profile names, and other details.
Clubhouse did not immediately respond to Insider's request for comment that was made on Saturday. As Cyber News reported, the exposed data could enable bad actors to target users through
phishing
schemes or identity theft.
The invite-only social media app launched in March 2020 and has grown into a popular platform and attracted millions of users. Its audio community allows users to tune into conversations, or "rooms," about various topics. The company is reportedly in talks for a funding round that values the company at $4 billion. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
A zero-day vulnerability in Zoom which can be used to launch remote code execution (RCE) attacks has been disclosed by researchers.
Why some governments are getting cyber crime gangs to do their hacking for them (ZDNet YouTube)
Pwn2Own, organized by the Zero Day Initiative, is a contest for white-hat cybersecurity professionals and teams to compete in the discovery of bugs in popular software and services.
The latest competition included 23 entries, competing in different categories including web browsers, virtualization software, servers, enterprise communication, and local escalation of privilege.
For successful entrants, the financial rewards can be high -- and in this case, Daan Keuper and Thijs Alkemade earned themselves $200,000 for their Zoom discovery.
The researchers from Computest demonstrated a three-bug attack chain that caused an RCE on a target machine, and all without any form of user interaction. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=ZOOM https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Three recently unearthed vulnerabilities in the Linux kernel, located in the iSCSI module used for accessing shared data storage facilities, could allow root privileges to anyone with a user account.
The trio of flaws – CVE-2021-27363, CVE-2021-27364 and CVE-2021-27365 – have lurked in Linux code since 2006 without detection until GRIMM researchers discovered them.
“If you already had execution on a box, either because you have a user account on the machine, or you’ve compromised some service that doesn’t have repaired permissions, you can do whatever you want basically,” said Adam Nichols, principal of the Software Security practice at GRIMM.
While the vulnerabilities “are in code that is not remotely accessible, so this isn’t like a remote exploit,” said Nichols, they are still troublesome. They take “any existing threat that might be there. It just makes it that much worse,” he explained. “And if you have users on the system that you don’t really trust with root access it, it breaks them as well.”
Referring to the theory that ‘many eyes make all bugs shallow,’ Linux code “is not getting many eyes or the eyes are looking at it and saying that seems fine,” said Nichols. “But, [the bugs] have been in there since the code was first written, and they haven’t really changed over the last 15 years.” Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Rising Linux security developer Alexander Popov of London-based Positive Technologies discovered and fixed a set of five security holes in the Linux kernel's virtual socket implementation. An attacker could use these vulnerabilities (CVE-2021-26708) to gain root access and knock out servers in a Denial of Service (DoS) attack.
With a Common Vulnerability Scoring System (CVSS) v3 base score of 7.0, high severity, smart Linux administrators will patch their systems as soon as possible.
While Popov discovered the bugs in Red Hat's community Linux distribution Fedora 33 Server, it exists in the system using the Linux kernel from November 2019's version 5.5 to the current mainline kernel version 5.11-rc6. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
A British security researcher has discovered today that a recent security flaw in the Sudo app also impacts the macOS operating system, and not just Linux and BSD, as initially believed.
The vulnerability, disclosed last week as CVE-2021-3156 (aka Baron Samedit) by security researchers from Qualys, impacts Sudo, an app that allows admins to delegate limited root access to other users.
Qualys researchers discovered that they could trigger a "heap overflow" bug in the Sudo app to change the current user's low-privileged access to root-level commands, granting the attacker access to the whole system.
The only condition to exploit this bug was that an attacker gain access to a system, which researchers said could be done by either planting malware on a device or brute-forcing a low-privileged service account. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux
|

|
Scooped by
Gust MEES
|
An information disclosure vulnerability in the Linux kernel can be exploited to leak data and act as a springboard for further compromise.
Disclosed by Cisco Talos researchers on Tuesday, the bug is described as an information disclosure vulnerability "that could allow an attacker to view Kernel stack memory."
The kernel is a key component of the open source Linux operating system. The vulnerability, tracked as CVE-2020-28588, was found in the proc/pid/syscall functionality of 32-bit ARM devices running the OS.
According to Cisco, the issue was first found in a device running on Azure Sphere. Attackers seeking to exploit the security flaw could read the /syscall OS file via Proc, a system used for interfacing between kernel data structures. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Large-scale data leaks have become almost a rite of passage for new social networks. If Clubhouse wasn't part of the, erm, club before, it is now.
Cyber News reported over the weekend that personal data for around 1.3 million users was scraped from the trendy voice chatroom app and posted on a hacker forum. The compromised data included names, handles for other linked social media accounts, and the username of whoever invited said user, as Clubhouse is still in an invite-only stage.
Clubhouse didn't immediately respond to Mashable's request for comment, but the official Clubhouse Twitter account pushed back against the idea that there was a hack, saying the leaked information is already public via the app's API. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Der Hackerwettbewerb Pwn2own stand dieses Jahr ganz im Zeichen der Coronapandemie. Gehackt wurde das Videokonferenzsystem Zoom, aber auch Betriebssysteme wie Windows 10 von Microsoft oder der Chrome-Browser von Google. Veranstaltet wird der Wettbewerb durch die Zero Day Initiative (ZDI).
Auf einem Rechner mit dem Videokonferenzsystem Zoom gelang es Daan Keuper und Thijs Alkemade, Schadcode aus der Ferne auszuführen - ohne jegliche Benutzerinteraktion. Dazu kombinierten sie gleich drei neue Sicherheitslücken in der Videokonferenzsoftware. Da die Lücken noch nicht geschlossen wurden, gibt es keine weiteren technischen Details zu den Zero Days.
In einer Animation des Angriffs wird jedoch gezeigt, dass die Sicherheitsforscher das Taschenrechnerprogramm auf dem angegriffenen Rechner öffnen konnten. Der Angriff soll sowohl unter Windows als auch unter MacOS funktionieren, auf iOS und Android wurde er noch nicht getestet. Die beiden Sicherheitsforscher erhalten 200.000 US-Dollar Preisgeld
Laut dem Zoom-Hersteller muss der Angriff "von einem akzeptierten externen Kontakt ausgehen oder Teil des gleichen Organisationskontos des Ziels sein". An einem Patch werde gearbeitet. "Als Best Practice empfiehlt Zoom allen Nutzern, nur Kontaktanfragen von Personen zu akzeptieren, die sie kennen und denen sie vertrauen." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=ZOOM https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Researchers say the new RedXOR backdoor is targeting Linux systems with various data exfiltration and network traffic tunneling capabilities.
Researchers have discovered a new backdoor targeting Linux systems, which they link back to the Winnti threat group.
The backdoor is called RedXOR – in part because its network data-encoding scheme is based on the XOR encryption algorithm, and in part because its samples were found on an old release of the Red Hat Enterprise Linux platform. The latter fact provides a clue that RedXOR is utilized in targeted attacks against legacy Linux systems, noted researchers.
The malware has various malicious capabilities, said researchers – from exfiltrating data to tunneling network traffic to another destination. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
CERTFR-2021-AVI-138 : Multiples vulnérabilités dans le noyau Linux de SUSE (22 février 2021)
De multiples vulnérabilités ont été découvertes dans le noyau Linux de SUSE. Certaines d'entre elles permettent à un attaquant de provoquer un problème de sécurité non spécifié par l'éditeur, une exécution de code arbitraire et un déni de service. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
A major vulnerability impacting a large chunk of the Linux ecosystem has been patched today in Sudo, an app that allows admins to delegate limited root access to other users.
The vulnerability, which received a CVE identifier of CVE-2021-3156, but is more commonly known as "Baron Samedit," was discovered by security auditing firm Qualys two weeks ago and was patched earlier today with the release of Sudo v1.9.5p2.
In a simple explanation provided by the Sudo team today, the Baron Samedit bug can be exploited by an attacker who has gained access to a low-privileged account to gain root access, even if the account isn't listed in /etc/sudoers — a config file that controls which users are allowed access to su or sudo commands in the first place. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux
|



 Your new post is loading...
Your new post is loading...







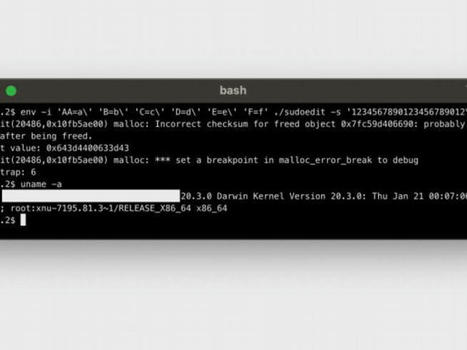










The Hive ransomware gang now also encrypts Linux and FreeBSD using new malware variants specifically developed to target these platforms.
However, as Slovak internet security firm ESET discovered, Hive's new encryptors are still in development and still lack functionality.
The Linux variant also proved to be quite buggy during ESET's analysis, with the encryption completely failing when the malware was executed with an explicit path.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux