A cryptocurrency-mining malware began exploiting a leaked NSA vulnerability several weeks before WannaCry sank its teeth into it.
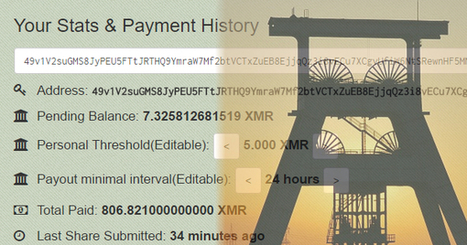
The researchers expected to see the ransom message above when they looked at a lab machine vulnerable to EternalBlue. Instead they found a subtler threat: Adylkuzz.
This malware relies on virtual private servers scanning the Internet on TCP port 445 for distribution. If infection proves successful, it enlists victims in a cryptocurrency-mining botnet. But Adylkuzz isn't interested in sharing an affected computer that's capable of communicating over Microsoft's Microsoft Server Message Block (SMB).
Security researcher Kafeine elaborates on that point:
"Upon successful exploitation via EternalBlue, machines are infected with DoublePulsar. The DoublePulsar backdoor then downloads and runs Adylkuzz from another host. Once running, Adylkuzz will first stop any potential instances of itself already running and block SMB communication to avoid further infection. It then determines the public IP address of the victim and download the mining instructions, cryptominer, and cleanup tools."
In that sense, Adylkuzz blocks other threats like WannaCry from leveraging ExternalBlue to infect vulnerable computers.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Adylkuzz
http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet



 Your new post is loading...
Your new post is loading...






A cryptocurrency-mining malware began exploiting a leaked NSA vulnerability several weeks before WannaCry sank its teeth into it.
The researchers expected to see the ransom message above when they looked at a lab machine vulnerable to EternalBlue. Instead they found a subtler threat: Adylkuzz.
This malware relies on virtual private servers scanning the Internet on TCP port 445 for distribution. If infection proves successful, it enlists victims in a cryptocurrency-mining botnet. But Adylkuzz isn't interested in sharing an affected computer that's capable of communicating over Microsoft's Microsoft Server Message Block (SMB).
Security researcher Kafeine elaborates on that point:
In that sense, Adylkuzz blocks other threats like WannaCry from leveraging ExternalBlue to infect vulnerable computers.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Adylkuzz
http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet