 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Cybersecurity experts believe CVE-2021-44228, a remote code execution flaw in Log4j, will take months, if not years, to address due its ubiquity and ease of exploitation.
Steve Povolny, head of advanced threat research for McAfee Enterprise and FireEye, said Log4Shell "now firmly belongs in the same conversation as Shellshock, Heartbleed, and EternalBlue."
"Attackers began by almost immediately leveraging the bug for illegal crypto mining, or using legitimate computing resources on the Internet to generate cryptocurrency for financial profit... Further exploitation appears to have pivoted towards theft of private information," Povolny told ZDNet.
"We fully expect to see an evolution of attacks." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Log4j

|
Scooped by
Gust MEES
|
Offenbar standen Daten von mehr als der Hälfte aller Facebook-Nutzer im Darknet zum Verkauf. 1,5 Milliarden Accounts sollen betroffen sein. Es handelt sich dabei wohl um Informationen wie E-Mailadressen, Wohnorte und die persönliche User-ID. Passwörter solle nicht dabei gewesen sein.
Es handelt sich dabei wahrscheinlich nicht um einen Hack oder eine andere Art von Diebstahl. Die Daten sollen laut "Privacy Affairs" via Scraping gesammelt worden sein. Dabei handelt sich um eine Technik, die öffentliche Informationen sammelt und einordnet bzw. kombiniert. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Auf einem Imageboard hat eine Gruppe Unbekannter mitgeteilt, dass sie Twitch "komplett" gehackt haben. In ihrem ersten Leak sollen sich fast 6000 Git-Repositories mit dem Quellcode der Mobil-, Desktop- und Konsolen-Apps von Twitch befinden. Die Daten enthalten darüber hinaus offenbar die Auszahlungen von Twitch an ihre Streamer.
"Die Community ist eine giftige Jauchegrube, daher wollen wir den Betrieb stören und die Konkurrenz im Online-Streaming-Markt fördern", erklären die Unbekannten ihre Motivation. Twitch hat sich bisher nicht zu dem Leak geäußert. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Twitch-Leak

|
Scooped by
Gust MEES
|
Microsoft has continued its analysis of the LemonDuck malware, known for installing crypto-miners in enterprise environments. It makes a strong case for why it is worth removing it from your network.
This group, according to Microsoft, has a well-stocked arsenal of hacking tools, tricks and exploits aimed at one thing: for their malware to retain exclusive access to a compromised network for as long as possible.
While crypto-mining malware could be just a nuisance, LemonDuck attributes suggest the attacker group really do try to own compromised networks by disabling anti-malware, removing rival malware, and even automatically patching vulnerabilities -- a competitive effort to keep rival attackers from feeding off its turf. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Google Could have unveiled a public preview of Cloud Armor's Adaptive Protection -- a machine learning-powered method of detecting and protecting enterprise applications and services from Layer 7 DDoS attacks.
It's the same technology that Google uses to provide Project Shield, a free service from Google parent Alphabet that protects human rights, government and media organizations against DDoS attacks. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?tag=DDos...

|
Scooped by
Gust MEES
|
Microsoft hat Notfallpatches für eine Sicherheitslücke mit dem Namen Printnightmare veröffentlicht. Ein Problem mit dem Druck-Spooler ermöglichte es Angreifern, Code aus der Ferne auszuführen.
Über die Remote Code Execution könnten Angreifer weitere Programme installieren oder Nutzerkonten mit Administratorrechten erstellen. Zunächst war für das Problem kein Patch verfügbar. Offenbar veröffentlichten Sicherheitsforscher versehentlich einen Proof-of-Concept für einen Exploit, der sich weiterhin ausnutzen ließ. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Windows https://www.scoop.it/topic/securite-pc-et-internet/?&tag=PrintNightmare

|
Scooped by
Gust MEES
|
IF YOU DON'T have enough to worry about already, consider a world where AIs are hackers.
Hacking is as old as humanity. We are creative problem solvers. We exploit loopholes, manipulate systems, and strive for more influence, power, and wealth. To date, hacking has exclusively been a human activity. Not for long.
As I lay out in a report I just published, artificial intelligence will eventually find vulnerabilities in all sorts of social, economic, and political systems, and then exploit them at unprecedented speed, scale, and scope. After hacking humanity, AI systems will then hack other AI systems, and humans will be little more than collateral damage. Learn more / En svoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=AI

|
Scooped by
Gust MEES
|
Attackers could use critical firmware vulnerabilities discovered by Microsoft in some NETGEAR router models as a stepping stone to move laterally within enterprise networks.
The security flaws impact DGN2200v1 series routers running firmware versions before v1.0.0.60 and compatible with all major DSL Internet service providers.
They allow unauthenticated attackers to access unpatched routers' management pages via authentication bypass, gain access to secrets stored on the device, and derive saved router credentials using a cryptographic side-channel attack. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?tag=Router

|
Scooped by
Gust MEES
|
Researchers have discovered a strain of cryptocurrency-mining malware that abuses Windows Safe mode during attacks.
After finding reports on Reddit of Avast antivirus users querying the sudden loss of the antivirus software from their system files, the team conducted an investigation into the situation, realizing it was due to a malware infection.
Crackonosh has been in circulation since at least June 2018. Once a victim executes a file they believe to be a cracked version of legitimate software, the malware is also deployed. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Unknown threat actors have been employing a Windows rootkit for years to stealthily install backdoors on vulnerable machines.
In a campaign dubbed Operation TunnelSnake by Kaspersky researchers, the team said on Thursday that an advanced persistent threat (APT) group, origin unknown but suspected of being Chinese-speaking, has used the rootkit to quietly take control of networks belonging to organizations.
Rootkits are packages of tools that are designed to stay under the radar by hiding themselves in deep levels of system code. Rootkits can range from malware designed to attack the kernel to firmware, or memory, and will often operate with high levels of privilege.
According to Kaspersky, the newly-discovered rootkit, named Moriya, is used to deploy passive backdoors on public-facing servers. The backdoors are then used to establish a connection -- quietly -- with a command-and-control (C2) server controlled by the threat actors for malicious purposes.
The backdoor allows attackers to monitor all traffic, incoming and outgoing, that passes through an infected machine and filter out packets sent for the malware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
A malware campaign with the aim of stealing passwords, bank details and other sensitive information is spreading quickly through Android devices.
Known as FluBot, the malware is installed via text messages claiming to be from a delivery company that asks users to click a link to track a package delivery. This phishing link asks users to install an application to follow the fake delivery – but the app is actually malware for stealing information from infected Android smartphones.
Once installed, FluBot also gains access to the victim's address book, allowing it to send the infected text message to all their contacts, further spreading the malware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
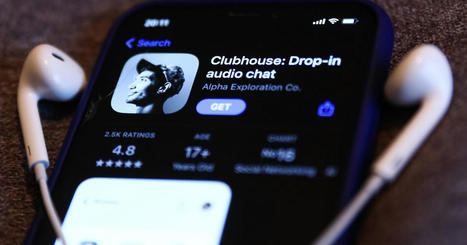
Large-scale data leaks have become almost a rite of passage for new social networks. If Clubhouse wasn't part of the, erm, club before, it is now.
Cyber News reported over the weekend that personal data for around 1.3 million users was scraped from the trendy voice chatroom app and posted on a hacker forum. The compromised data included names, handles for other linked social media accounts, and the username of whoever invited said user, as Clubhouse is still in an invite-only stage.
Clubhouse didn't immediately respond to Mashable's request for comment, but the official Clubhouse Twitter account pushed back against the idea that there was a hack, saying the leaked information is already public via the app's API. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Der Hackerwettbewerb Pwn2own stand dieses Jahr ganz im Zeichen der Coronapandemie. Gehackt wurde das Videokonferenzsystem Zoom, aber auch Betriebssysteme wie Windows 10 von Microsoft oder der Chrome-Browser von Google. Veranstaltet wird der Wettbewerb durch die Zero Day Initiative (ZDI).
Auf einem Rechner mit dem Videokonferenzsystem Zoom gelang es Daan Keuper und Thijs Alkemade, Schadcode aus der Ferne auszuführen - ohne jegliche Benutzerinteraktion. Dazu kombinierten sie gleich drei neue Sicherheitslücken in der Videokonferenzsoftware. Da die Lücken noch nicht geschlossen wurden, gibt es keine weiteren technischen Details zu den Zero Days.
In einer Animation des Angriffs wird jedoch gezeigt, dass die Sicherheitsforscher das Taschenrechnerprogramm auf dem angegriffenen Rechner öffnen konnten. Der Angriff soll sowohl unter Windows als auch unter MacOS funktionieren, auf iOS und Android wurde er noch nicht getestet. Die beiden Sicherheitsforscher erhalten 200.000 US-Dollar Preisgeld
Laut dem Zoom-Hersteller muss der Angriff "von einem akzeptierten externen Kontakt ausgehen oder Teil des gleichen Organisationskontos des Ziels sein". An einem Patch werde gearbeitet. "Als Best Practice empfiehlt Zoom allen Nutzern, nur Kontaktanfragen von Personen zu akzeptieren, die sie kennen und denen sie vertrauen." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=ZOOM https://www.scoop.it/topic/securite-pc-et-internet
|

|
Scooped by
Gust MEES
|
The Hive ransomware gang now also encrypts Linux and FreeBSD using new malware variants specifically developed to target these platforms.
However, as Slovak internet security firm ESET discovered, Hive's new encryptors are still in development and still lack functionality.
The Linux variant also proved to be quite buggy during ESET's analysis, with the encryption completely failing when the malware was executed with an explicit path.

|
Scooped by
Gust MEES
|
An unknown hacker has leaked the entirety of Twitch's source code among a 125GB trove of data released this week.
The hack, first reported by Video Games Chronicle and confirmed by multiple sources, includes:
The entirety of twitch.tv, with commit history going back to its early beginnings
Mobile, desktop and console Twitch clients
Creator payout reports from 2019
Proprietary SDKs and internal AWS services used by Twitch
Every other property that Twitch owns including IGDB and CurseForge
An unreleased Steam competitor, codenamed Vapor, from Amazon Game Studios
Twitch SOC internal red teaming tools
The hacker, who called themselves "Anonymous" on a 4chan discussion board, said Twitch's community is "a disgusting toxic cesspool, so to foster more disruption and competition in the online video streaming space, we have completely pwned them, and in part one, are releasing the source code from almost 6,000 internal Git repositories." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Twitch-Leak

|
Scooped by
Gust MEES
|
Sensitive data including COVID-19 vaccination statuses, social security numbers and email addresses have been exposed due to weak default configurations for Microsoft Power Apps, according to Upguard.
Upguard Research disclosed multiple data leaks exposing 38 million data records via Microsoft Power Apps portals configured to allow public access.
The data leaks impacted American Airlines, Microsoft, J.B. Hunt and governments of Indiana, Maryland and New York City. Upguard first discovered the issue involving the ODdata API for a Power Apps portal on May 24 and submitted a vulnerability report to Microsoft June 24.
According to Upguard, the primary issue is that all data types were public when some data like personal identifying information should have been private. Misconfiguration led to some private data being surfaced.
Microsoft Power Apps are low-code tools to design apps and create public and private web sites. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Microsoft is warning customers about the LemonDuck crypto mining malware which is targeting both Windows and Linux systems and is spreading via phishing emails, exploits, USB devices, and brute force attacks, as well as attacks targeting critical on-premise Exchange Server vulnerabilities uncovered in March.
The group was discovered to be using Exchange bugs to mine for cryptocurrency in May, two years after it first emerged.
Notably, the group behind LemonDuck is taking advantage of high-profile security bugs by exploiting older vulnerabilities during periods where security teams are focussed on patching critical flaws, and even removing rival malware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Die Telefonnummern und Kontakte aller Clubhouse-Konten werden wohl im Darknet angeboten. Nummern werden nach ihrer Wichtigkeit eingestuft.
Clubhouse scheint nicht allzu abgesichert zu sein.
(Bild: Pixabay.com/Montage: Golem.de/Pixabay License)
Offenbar hat ein Angreifer Zugang zu allen Telefonnummern erhalten können, die sich mit der App Clubhouse registriert haben. Zusätzlich dazu will er oder sie die gespeicherten Kontakte aller 10 Millionen User erhalten haben. Insgesamt 3,8 Milliarden Telefonnummern, darunter Festnetz, private, geschäftliche und Mobilfunknummern umfasst der Datensatz. Das berichtet der Security-Forscher Marc Ruef auf Twitter. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
As IoT devices like Amazon Echo become more and more popular, it isn’t unusual for users to re-sell them. Indeed, it’s increasingly common to come across them on eBay or even at the occasional yard sale. Amazon suggests that, when users are done with a product, they factory reset the device so as to erase any personal information stored within it before sending it back out into the world.
However, it would appear that simply resetting your device won’t actually expunge that data from the face of the Earth and that reselling your device could hypothetically lead to your old information getting boosted.
Researchers with Northeastern University recently spent 16 months buying and reverse engineering 86 used Amazon Echo Dot devices in an attempt to understand any security deficiencies they might have. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things https://www.scoop.it/topic/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
Microsoft has assigned CVE-2021-34527 to the print spooler remote code execution vulnerability known as "PrintNightmare" and confirmed that the offending code is lurking in all versions of Windows.
The megacorp said it was still investigating whether the vulnerability was exploitable in every version, but domain controllers are indeed affected.
Microsoft also confirmed that this nasty was distinct from CVE-2021-1675, which was all about a different attack vector and a different vulnerability in RpcAddPrinterDriverEx(). The June 2021 Security update dealt with that, according to Microsoft, and did not introduce the new badness. That had existed prior to the update.
The Windows giant also confirmed that the PrintNightmare vulnerability was being exploited in the wild. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Windows https://www.scoop.it/topic/securite-pc-et-internet/?&tag=PrintNightmare

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A major security flaw in Dell’s firmware updating and operating recovery software, BIOSConnect, potentially exposes tens of millions of devices that Dell preinstalled it on.
BleepingComputer reported on Thursday that researchers with security firm Eclypsium discovered a flaw in BIOSConnect, which is part of Dell’s standard SupportAssist software and updates the firmware on a computer’s system board, that could allow attackers to remotely execute malicious code. In a report, the researchers wrote that the vulnerability was so severe it could “enable adversaries to control the device’s boot process and subvert the operating system and higher-layer security controls,” which would give them control “over the most privileged code on the device.”
There are four separate vulnerabilities, one of which involves insecure connections between a BIOS being updated and Dell’s servers that allow an attacker to redirect the machine to a maliciously modified update package. The remaining three are classified as overflow vulnerabilities. Eclypsium rated the bugs as severe security threats. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
An information disclosure vulnerability in the Linux kernel can be exploited to leak data and act as a springboard for further compromise.
Disclosed by Cisco Talos researchers on Tuesday, the bug is described as an information disclosure vulnerability "that could allow an attacker to view Kernel stack memory."
The kernel is a key component of the open source Linux operating system. The vulnerability, tracked as CVE-2020-28588, was found in the proc/pid/syscall functionality of 32-bit ARM devices running the OS.
According to Cisco, the issue was first found in a device running on Azure Sphere. Attackers seeking to exploit the security flaw could read the /syscall OS file via Proc, a system used for interfacing between kernel data structures. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Clubhouse CEO Paul Davison said Sunday that a report claiming personal user data had been leaked was “false.” Cyber News reported a SQL database with users’ IDs, names, usernames, Twitter and Instagram handles and follower counts were posted to an online hacker forum. According to Cyber News, it did not appear that sensitive user information such as credit card numbers were among the leaked info.
Clubhouse did not immediately reply to a request for more information from The Verge on Sunday. But Davison said in response to a question during a town hall that the platform had not suffered a data breach. “No, This is misleading and false, it is a clickbait article, we were not hacked. The data referred to was all public profile information from our app. So the answer to that is a definitive ‘no.’” Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|
The personal data of 1.3 million Clubhouse users has leaked online on a popular hacker forum, according to a Saturday report from Cyber News.
The leaked data of Clubhouse users includes names, social media profile names, and other details.
Clubhouse did not immediately respond to Insider's request for comment that was made on Saturday. As Cyber News reported, the exposed data could enable bad actors to target users through
phishing
schemes or identity theft.
The invite-only social media app launched in March 2020 and has grown into a popular platform and attracted millions of users. Its audio community allows users to tune into conversations, or "rooms," about various topics. The company is reportedly in talks for a funding round that values the company at $4 billion. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Clubhouse https://www.scoop.it/topic/social-media-and-its-influence https://www.scoop.it/topic/securite-pc-et-internet
|



 Your new post is loading...
Your new post is loading...




























Cybersecurity experts believe CVE-2021-44228, a remote code execution flaw in Log4j, will take months, if not years, to address due its ubiquity and ease of exploitation.
Steve Povolny, head of advanced threat research for McAfee Enterprise and FireEye, said Log4Shell "now firmly belongs in the same conversation as Shellshock, Heartbleed, and EternalBlue."
"Attackers began by almost immediately leveraging the bug for illegal crypto mining, or using legitimate computing resources on the Internet to generate cryptocurrency for financial profit... Further exploitation appears to have pivoted towards theft of private information," Povolny told ZDNet.
"We fully expect to see an evolution of attacks."
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Log4j