This zero-day exploit dubbed Thunderstrike 2 targets your Mac’s firmware thanks to an attached Thunderbolt accessory, such as an Ethernet adaptor or an external hard drive. After receiving the code via a phishing email or a malicious web site, malware code could look for connected Thunderbolt accessories and flash their option ROMs.
If you reboot your Mac with this infected Thunderbolt accessory plugged in, the EFI will execute the option ROM before booting OS X. As this option ROM has been infected, it will execute malicious code infecting the EFI itself. For example, it could simply make your Mac’s firmware refuse to boot OS X, turning your Mac into a useless machine. And if your firmware is compromised, there is no way to boot OS X, update the firmware and remove the malicious code.
The best part of this zero-day vulnerability is that your Thunderbolt accessory remains infected. If you plug your Ethernet adaptor into a new Mac, this Mac will get infected as well when it reboots. It’s not as harmful as malware that spreads through the Internet, but it could make some serious damage in an office environment for example.
Image credit (posted on Facebook) <===> http://www.pcworld.com/article/2955707/security/macs-can-be-remotely-infected-with-firmware-malware-that-remains-after-reformatting.html
Mehr erfahren / En savoir plus / Learn more:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Thunderstrike



 Your new post is loading...
Your new post is loading...







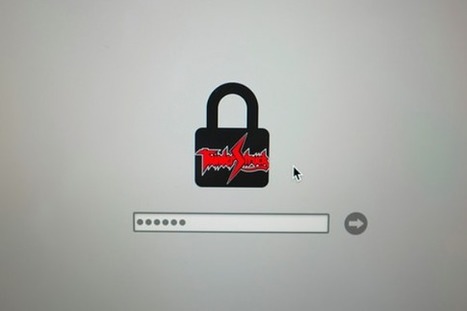






Image credit (posted on Facebook) <===> http://www.pcworld.com/article/2955707/security/macs-can-be-remotely-infected-with-firmware-malware-that-remains-after-reformatting.html
Mehr erfahren / En savoir plus / Learn more:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Thunderstrike