Rombertik is designed to steal any plain text entered into a browser window
A new type of malware resorts to crippling a computer if it is detected during security checks, a particularly catastrophic blow to its victims.
The malware, nicknamed Rombertik by Cisco Systems, is designed to intercept any plain text entered into a browser window. It is being spread through spam and phishing messages, according to Cisco’s Talos Group blog on Monday.
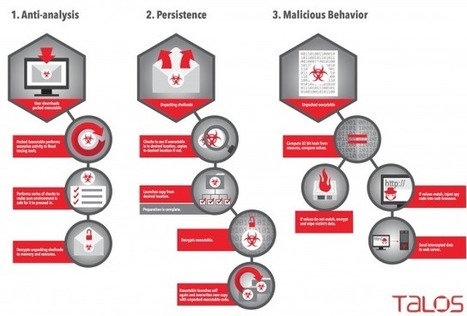
Rombertik goes through several checks once it is up and running on a Windows computer to see if it has been detected.
That behavior is not unusual for some types of malware, but Rombertik “is unique in that it actively attempts to destroy the computer if it detects certain attributes associated with malware analysis,” wrote Ben Baker and Alex Chiu of the Talos Group.
Such “wiper” malware has been used in the past, notably against South Korean targets in 2013 and against Sony Pictures Entertainment last year, an attack attributed to North Korea by the U.S. government.
The last check Rombertik does is the most dangerous one. It computes a 32-bit hash of a resource in memory, and if either that resource or the compile time had been changed, Rombertik triggers self-destruct.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Rombertik



 Your new post is loading...
Your new post is loading...

![8 Vulnerable Software Apps Exposing Your Computer to Cyber Attacks [Infographic] | CyberSecurity | eSkills | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Manyk3R4XvcpHXxi11NTkTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
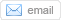
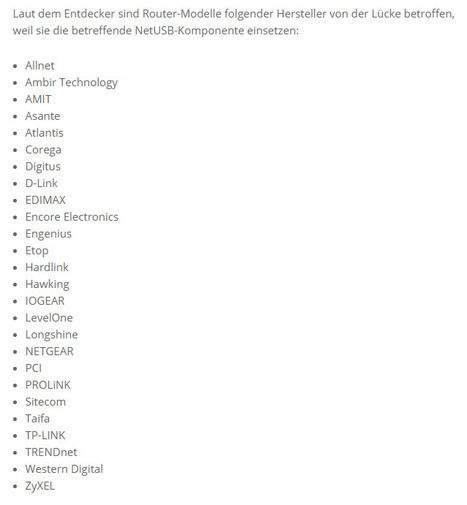



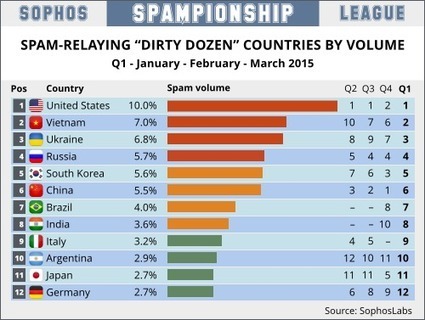


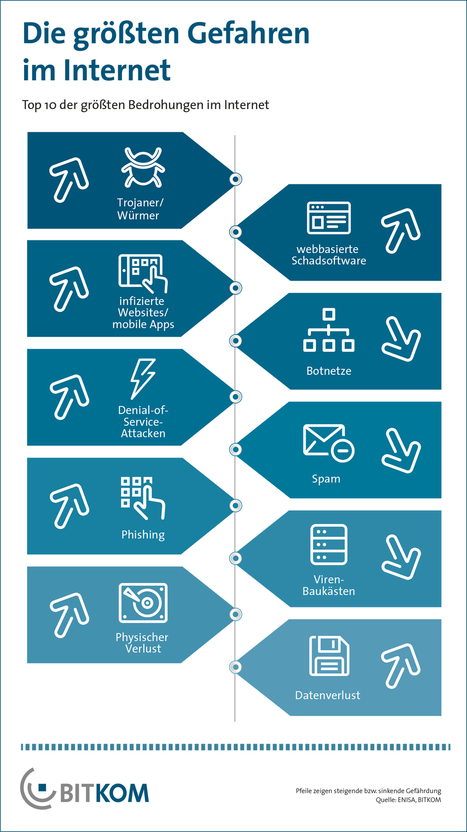


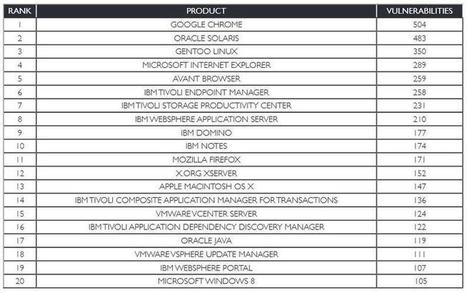















Are you at risk for cyber attacks? Check out this article to find out.