Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Related articles to 21st Century Learning and Teaching as also tools...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Elizabeth Milovidov's curator insight,
December 1, 2014 9:24 AM
Is your phone secure? Read these 10 tips for guidance.

Monty Bell's curator insight,
April 10, 2014 11:35 AM
A balanced discussion on a very contentious issue |

Gust MEES's curator insight,
November 17, 2014 8:26 AM
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more: 
Gust MEES's curator insight,
November 17, 2014 8:28 AM
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more:

Jacqueline Taylor-Adams's curator insight,
March 27, 2014 11:55 AM
We rescooped this article from our (the Urban Tech Fair's) Czar of Education, Bonnie Bracey Sutton who shared this thought provoking article. What say, ye? ______________________ Be part of the Access, Education, and Commerce movement, the Urban Tech Fair www.UrbanTechFair.org

Blue Jay Bridge's curator insight,
June 6, 2013 8:59 PM
I've seen folks asking for this info on twitter. Hope this helps.
Gary Harwell's curator insight,
April 3, 2013 12:47 AM
Is ti possible that we have a special room for this? |






![BYOD Pros and Cons in Education [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Ch1oqxgT1jQ06m3I7BtCdDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



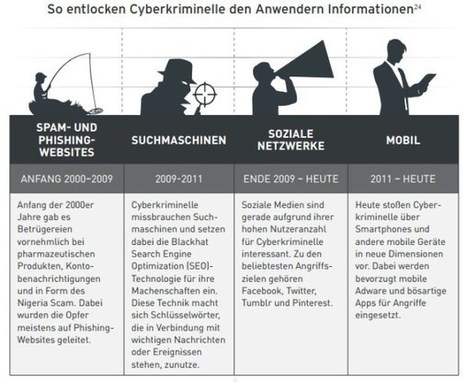
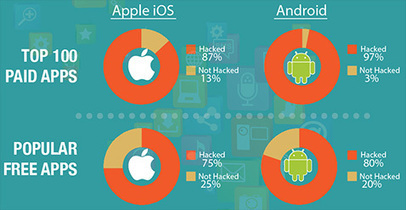










Learn more:
- https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
- https://gustmees.wordpress.com/?s=twitter
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Botnet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet